Setup
This guide will help you set up Calimero in your device.
There are two main paths:
- Install via Script or Homebrew (Recommended): Quickly install
merodfor most users. - Build from Source: For developers who want to contribute or modify the framework.
Supported Platforms
Calimero currently supports the following operating systems and architectures:
- Operating Systems: macOS, Linux
- Architectures: x86_64, arm64 (Apple Silicon)
If your platform is not supported, please create an issue on GitHub.
Installation
You can choose to install merod using either the installation script or
Homebrew.
- Homebrew
- Installation Script
If you use Homebrew, you can install merod directly with the following
steps:
Steps
-
Add the Calimero Homebrew tap:
brew tap calimero-network/homebrew-tap -
Install
merod:brew install merod -
Verify the installation:
merod --version
If the version number appears, the installation was successful.
The installation script supports multiple terminal environments and will automatically configure your PATH based on your shell.
Steps
-
Open your terminal and run:
curl -sSf https://raw.githubusercontent.com/calimero-network/install-sh/master/install-merod.sh | bash -
Source the updated PATH:
source <your-shell-config-file>Replace
<your-shell-config-file>with.bashrc,.zshrc, or the relevant configuration file for your shell. -
Verify the installation:
merod --version
If the version number appears, the installation was successful.
Notes for Shell Environments
The script automatically updates your PATH based on your shell configuration:
- Bash: Updates
.bashrc. - Zsh: Updates
.zshrc. - Fish: Modifies
~/.config/fish/config.fish. - Csh/Tcsh: Updates
.cshrc.
To apply the changes immediately, use the source command as described in step
2 above.
Next Steps
Initialize and run node
If this is your first time initializing the node, the process may take a little bit more time until all dependencies are downloaded. It will take around 7 minutes but can vary depending on your internet connection.
1. Initialize node
merod --node-name node1 init --server-port 2428 --swarm-port 2528
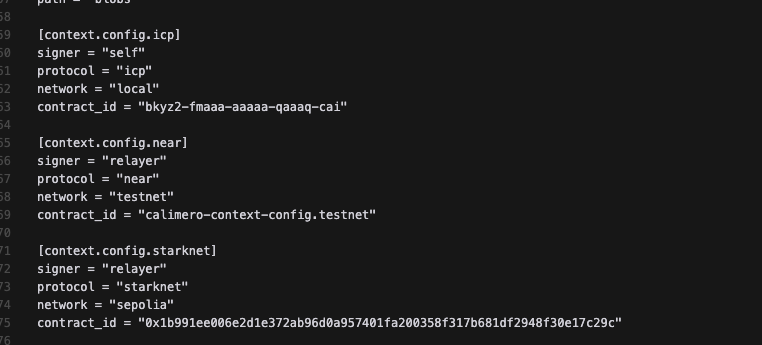
Node configuration file contains protocol defined metada. Node file is located
under ~/.calimero folder.
2. Run node
merod --node-name node1 run
Wait for a few moments and node logs should appear.
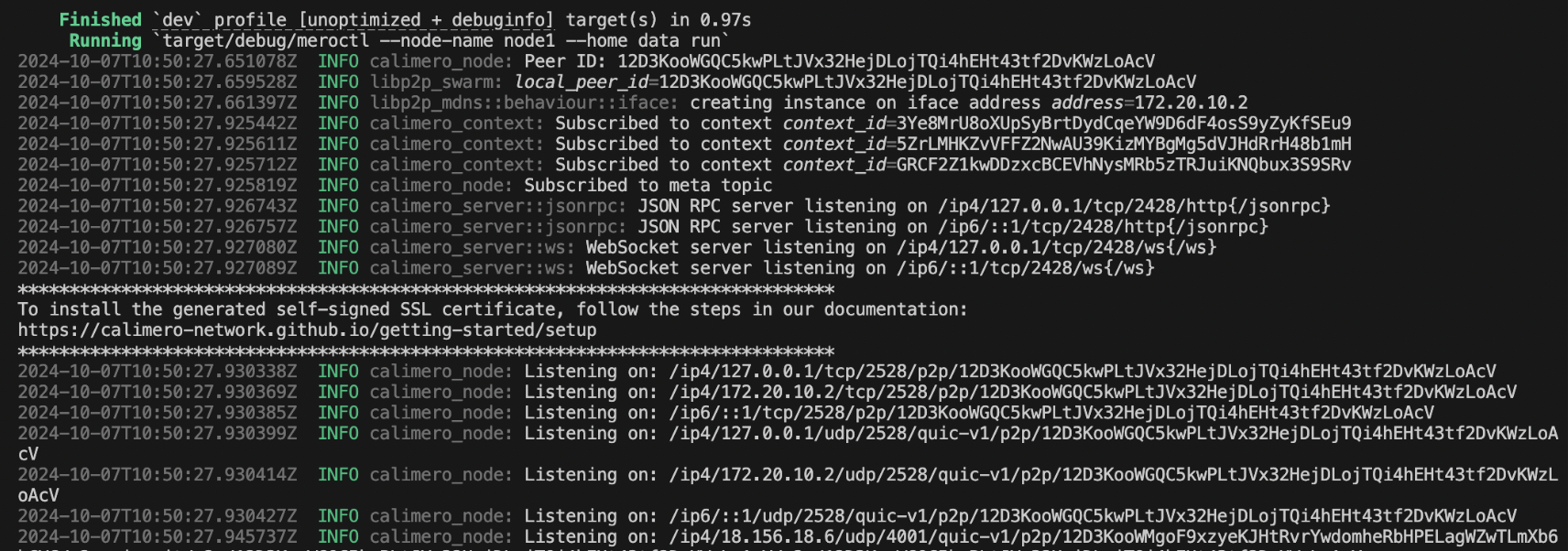
When you see something like this that means that node is now ready for use.